If the tech world needed a reminder that regulation waits for no one, the European Union has provided it with gusto. It’s the new Cyber Resilience Act (CRA), a sprawling, far-reaching rulebook for product cybersecurity, that arrived this year with the subtlety of a freight train and the same relentless forward motion.
The Act requires manufacturers, software vendors, device makers, and anyone dabbling in connected technology to build security into products from day one and maintain it throughout their lifecycle. Sensible? Absolutely. Straightforward? Not quite. According to the latest ONEKEY IoT & OT Cybersecurity Report 2025, confusion over who is actually responsible for meeting these obligations is now one of the industry’s most significant vulnerabilities.
The report, from Düsseldorf-based cybersecurity specialist ONEKEY, surveyed 300 organisations across IoT and OT-heavy sectors — from robotics and industrial machinery to smart buildings and found a landscape still struggling to assign clear accountability.
Responsibility: Everyone’s Job, and No One’s Job
Nearly half of organisations surveyed (46 per cent) have parked CRA responsibility with their IT security teams. Fair enough. But the rest? They are all over the shop like a dropped box of screws.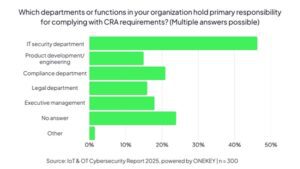
Compliance departments lead in 21% of companies. Top management takes charge in 18 per cent of cases. Legal teams step in for 16 per cent. Product development shoulders the task in 15 per cent. And engineering teams, despite carrying the actual burden of secure-by-design development, often watch from the sidelines.
“The responsibilities need to be more clearly defined and consolidated,” said Jan Wendenburg, CEO of ONEKEY. “The wide range of CRA stakeholders within the industry reflects the fact that the regulation itself covers a broad spectrum of topics.”
And he has a point: the CRA isn’t a narrow directive. It’s a full-funnel mandate covering design, development, testing, documentation, incident reporting, risk management and even the software supply chain.
Secure by Design: No Longer Optional
Manufacturers must now demonstrate “security by design”, meaning every internet-connected widget, robot, sensor, or industrial controller must be engineered to resist cyberattacks and continuously updated to remain safe.
“This is clearly an area where engineering and product development play a central role,” Wendenburg said.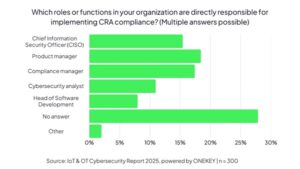
From day one until end-of-life, vendors must:
-
Provide regular security updates
-
Patch known vulnerabilities
-
Maintain comprehensive documentation
-
Deliver a Software Bill of Materials (SBOM)
-
Report any actively exploited vulnerability to ENISA and national CSIRTs within 24 hours
“That responsibility typically falls to the IT security department,” Wendenburg added, a subtle way of noting that most companies aren’t yet structured to respond in that timeframe.
And there are teeth behind these rules: violations of the CRA can result in penalties of up to €15 million or 2.5% of global annual turnover, whichever is higher. Enough to make even well-seasoned general counsels reach for the chamomile tea.
The SBOM Problem: Industry’s Weakest Link
Perhaps the most striking finding in the ONEKEY report is the startlingly low level of involvement by software development leaders. Only 8 per cent of organisations put CRA responsibility on the head of software development — despite the SBOM being one of the Act’s most critical requirements.
“The SBOM is the weakest link in the compliance chain for the Cyber Resilience Act,” Wendenburg said.
Under the Act, every connected product entering the EU market must provide a fully documented breakdown of every software component, libraries, frameworks, dependencies, versions, licences, and known vulnerabilities. Miss a single vulnerable component? The product may legally be blocked from market entry.
Given that more than 2,000 new software vulnerabilities emerge each month, manually maintaining accurate SBOMs is effectively impossible.
“Without automated verification, it’s practically impossible to manage,” Wendenburg said — not so much a warning as a statement of fact.
Industry Organisations Scramble to Structure Themselves
Given the Act’s complexity, ONEKEY also asked companies how they are structuring themselves to handle compliance. The responses show an industry only partway through its growing pains.
-
28% have set up cross-department working groups
-
13% have created dedicated CRA teams
-
32% have no formal structure at all
Among those with teams, headcounts vary wildly: some have three people, others more than ten, often spanning product development, vulnerability management, engineering, software security, compliance and legal.
“It’s encouraging that more than 40 percent of organizations have established some form of internal structure to manage CRA implementation,” Wendenburg said. “Ultimately, cybersecurity isn’t about ticking regulatory boxes — it’s about protecting the company from increasingly sophisticated cyberattacks with potentially dramatic consequences.”
In other words: compliance may be mandatory, but resilience is the real prize.
ONEKEY Steps Into the Gap
As companies wade through this new regulatory thicket, ONEKEY is positioning itself as a lifeline. Its fully automated Product & Cybersecurity Compliance Platform offers:
-
Automated SBOM generation
-
Vulnerability identification in minutes
-
Compliance verification
-
Lifecycle cybersecurity monitoring
-
“Digital Cyber Twins” for 24/7 post-release oversight
All without requiring source code access, a significant advantage for companies juggling complex supplier ecosystems.
For firms just beginning their CRA journey, the company also offers a CRA Readiness Assessment Workshop. Participants receive:
-
A hands-on introduction to the regulation
-
A personalised evaluation plan
-
A detailed review of software development processes
-
A gap analysis
-
A tailored roadmap for implementation
ONEKEY’s platform, combined with its consulting services, is already used by major manufacturers across Asia, Europe and the Americas. The company’s technology is backed by PwC Germany’s investment portfolio, a seal of confidence in its long-term relevance.
A Cross-Departmental Era Has Arrived
If one message rings through the report, it’s this: cybersecurity responsibilities can no longer be siloed. Engineering, legal, IT, compliance, software development and product management all share a piece of the burden, and none can function in isolation.
As Wendenburg put it:
“The Cyber Resilience Act is truly cross-departmental and cross-functional, which means responsibility within organizations is not immediately clear. What may first appear to be confusion over accountability is, on closer inspection, understandable. The challenge for industry lies in meeting the full scope of the EU regulation.”
Clear lines of accountability, then, aren’t just desirable; they’re fast becoming fundamental. And as the EU sharpens its focus, organisations that don’t adapt risk learning the hard way that cyber resilience is no longer a luxury. It’s the law.






















